By Danielle Guetta, Product Marketing Manager, CheckPoint | Source
Do you feel that your inbox is burdened with an increasing number of phisy-looking emails, now more than ever before? Well, that’s because it actually is.
According to Check Point Research Q3 Phishing Report, email-based phishing attacks saw the highest increase in number, compared to any other platform in Q2. The most common of these emails are impersonation emails asking users to reset or submit their Microsoft account credentials, in order to gain control over their accounts.
In Q3 of 2020, email was the most used platform for impersonation attacks, accounting for a staggering 44% of the attacks total, with Microsoft being the most imitated brand for impersonation phishing attempts (19% of total), followed by Google (9% of total).
So what does it mean for email security, especially in the new normal?
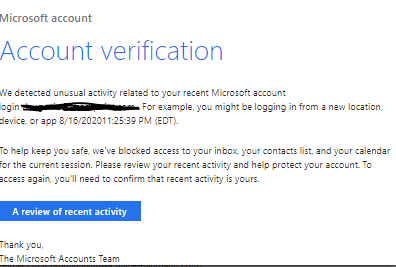 Figure 1: Account verification phishing email from “Microsoft Accounts Team”
Figure 1: Account verification phishing email from “Microsoft Accounts Team”Working from home is distracting, and cyber criminals know it
I believe most can relate to the next scenario: you are in the middle of a business call with your teammates on Zoom or Teams. Your kids are at home, and while you try to maintain your focus on your work call, your toddler is throwing his lunch on the carpet, while your dog has appointed itself the house’s vacuum cleaner.
In the middle of it all, you get an email from Microsoft saying that your account was blocked, and you have to verify your details ASAP. Sure, you might have been more cautious if you were at the office, undistracted by your kids, dogs, or spouse. However, in the midst of the chaos that is working from home, you clicked on that link and verified your account with your username and password, just so you can keep working. And just like that, you unknowingly fell victim to a phishing attack that harvested your account’s credentials.
The increase in phishing emails in Q3 of 2020 is one of the most prominent trends of the Work-From-Home era. Cybercriminals are well aware of the distractions people are dealing with while trying to work and be productive from home. Combined with the enormous amount of emails employees receive every day, the recipe for a successful email phishing campaign is complete.
What’s worse is that an email phishing attack is often the first step in a multi-staged attack that puts your entire organization at risk. When cybercriminals obtain one employee’s account credentials, they have access to corporate data, and can use the hijacked account to send further phishing emails to other employees in the organization, pretending to be the hijacked account’s owner. These attacks can results in huge costs, loss of sensitive data and even compliance fines, in case of a customer data breach.
To learn more about these types of attacks, we invite you to watch the following video where Maya Horwitz, Director of threat research and intelligence, takes you through one of the most interesting stories we uncovered – the Florentine Banker Group
Email security is crucial now more than ever
Check Point Research’s Report findings are yet another testament to the fact organizations can’t afford to compromise on email security, now more than ever. The new normal presents a reality that is not going to change in the near future, which means remote work is here to stay. Employees working from home, distracted by their daily life, can’t be relied on to stop the next email phishing attack, and that is why a pre-emptive email security solution must be deployed.
To make matters worse, in the new normal, phishing and malware threats do not stop at mailboxes. The productivity applications employees use daily from Microsoft 365 or Google Workspace are a direct extension of their mailboxes, and used to send sensitive files and complete important tasks involving corporate data all the time. For that, organizations must consider a solution that provides complete protection from all attacks for both email and productivity suite applications such as Teams, OneDrive, Google Drive and others.
Video | Part #7: What Can a Malicious Email Do?

























