Malicious actors are distributing a new backdoor, MadMxShell, through a Google Ads campaign that impersonates an IP scanner. This Windows backdoor leverages DNS MX queries for communication with its command-and-control server.
The technique involves encoding data within subdomains of DNS MX queries to send information to the attacker and receiving commands encoded within the response packets.
MadMxShell allows the attacker to collect system data, execute commands through the command prompt, and manipulate files on the compromised machine.
Advertisers are using malvertising, placing malicious ads disguised as legitimate software, to spread a sophisticated Windows backdoor called MadMxShell for the first time, which highlights a new tactic for delivering advanced malware.
Integrate ANY.RUN in Your Company for Effective Malware Analysis
Are you from SOC, Threat Research, or DFIR departments? If so, you can join an online community of 400,000 independent security researchers:
- Real-time Detection
- Interactive Malware Analysis
- Easy to Learn by New Security Team members
- Get detailed reports with maximum data
- Set Up Virtual Machine in Linux & all Windows OS Versions
- Interact with Malware Safely
If you want to test all these features now with completely free access to the sandbox:
The attackers exploited Google Ads by registering domains imitating popular IP scanner software, tricking users into downloading the backdoor, bypassing traditional malware detection methods and emphasizing the need for increased vigilance against malvertising.
An attacker leverages social engineering tactics to deceive a user searching for legitimate IP scanning tools, where the user is tricked into clicking on a malicious Google ad that directs them to a typosquatted domain mimicking a popular download site.
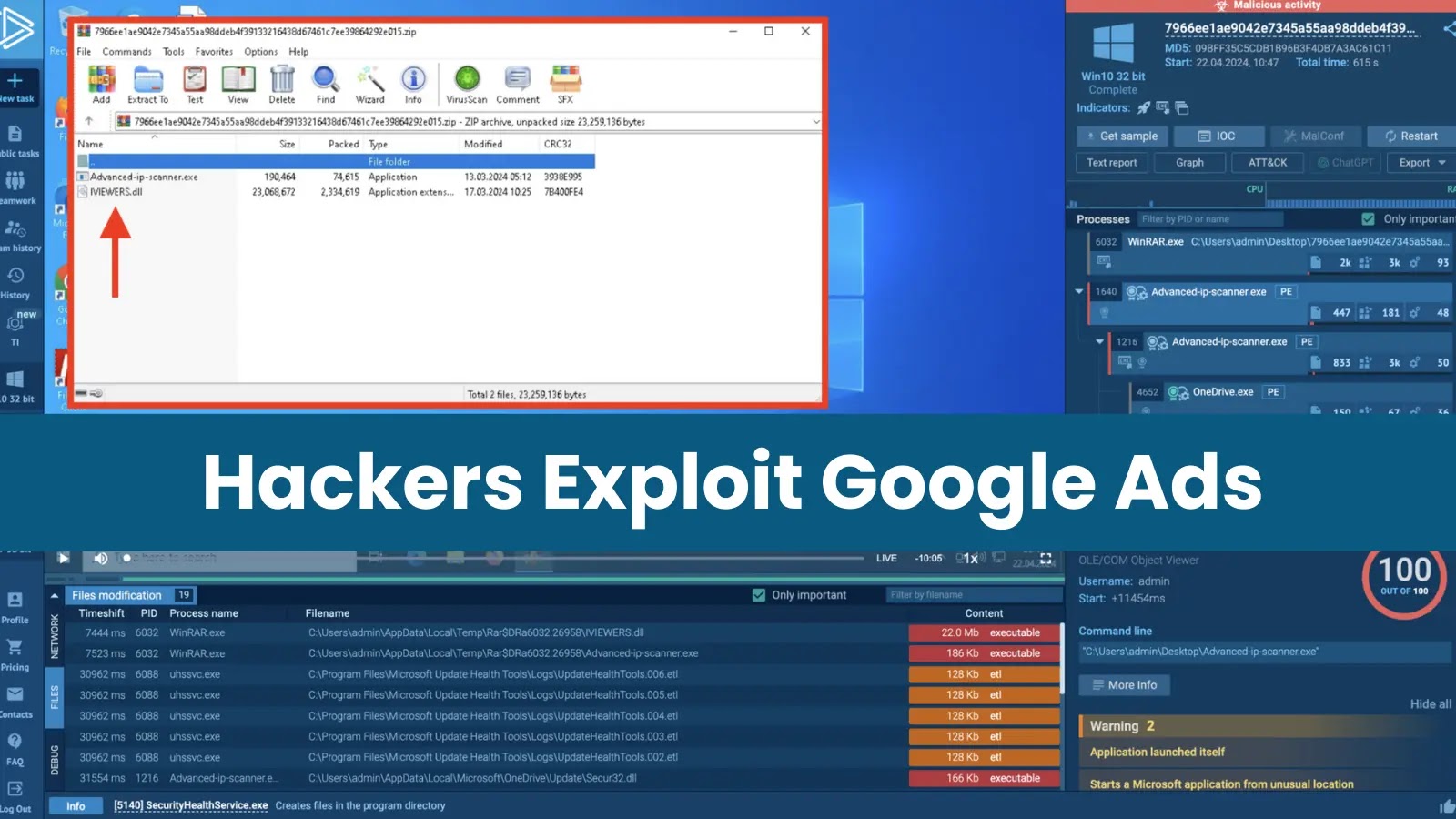
Upon clicking the download button on this fake site, a malicious ZIP archive disguised as a legitimate IP scanner (“Advanced-ip-scanner.zip”) is downloaded.
The archive contains two malicious files: “IVIEWERS.dll” and “Advanced-ip-scanner.exe”, which are likely designed to exploit vulnerabilities in the user’s system or establish persistence to maintain unauthorized access for malicious purposes.
Advanced-ip-scanner.exe leverages DLL side-loading to inject the malicious IVIEWERS.dll during execution, which then employs process hollowing to replace the legitimate memory of Advanced-ip-scanner.exe with its own malicious shellcode.
According to ANY.RUN, process hollowing allows malware to hijack a process effectively, allowing it to run undetected under the guise of a legitimate application.
MadMxShell, a backdoor malware, injects into Advanced-ip-scanner.exe and unpacks two files: a legitimate OneDrive.exe and a malicious Secur32.dll. It leverages OneDrive.exe’s trusted status to sideload Secur32.dll, which creates a persistent scheduled task and executes the backdoor shellcode.
To evade detection, MadMxShell employs multiple techniques, including DNS tunnelling for covert communication with its command-and-control server and multi-stage DLL loading to delay analysis, also runs a ping command through a separate Cmd.exe process, potentially slowing down analysis in automated sandboxes with limited lifespans.
ANY.RUN sandbox: see all aspects of malware behavior in real-time - Get started free
What is ANY.RUN?
ANY.RUN is a renowned ally for over 400,000 cybersecurity experts globally. This interactive sandbox platform streamlines the malware analysis process for threats aimed at both Windows and Linux systems, equipping analysts with a sophisticated tool for their investigative work.
Additionally, ANY.RUN’s threat intelligence offerings, namely Lookup and Feeds, deliver precise indicators of compromise and contextual insights that enable users to detect threats and manage incident responses swiftly.
ANY.RUN enhances the speed and accuracy of threat analysis. The platform is adept at identifying common malware families using YARA and Suricata rules and can pinpoint malware behaviors through signatures when specific family detection is unfeasible.
Key Features of ANY.RUN:
- Rapid Malware Detection: ANY.RUN can detect malware in approximately 40 seconds following a file upload. It utilizes YARA and Suricata rules to recognize well-known malware families and employs behavioral signatures to identify malicious activities in new threats.
- Real-Time Interaction with Samples: Powered by VNC, ANY.RUN’s interactive cloud sandbox allows users to perform real-system activities such as browsing web pages, navigating through installers, and accessing password-protected archives.
- Cost-Effective and Maintenance-Free: As a cloud-based solution, ANY.RUN eliminates the need for initial setup or ongoing maintenance, saving time and resources for businesses.
- Comprehensive Malware Behavior Analysis: ANY.RUN offers an in-depth examination of malware behavior, tracking network traffic, system calls, and file system modifications.
- Enhanced Team Collaboration: The platform facilitates easy sharing of analysis results among team members. Senior analysts can also review the work of junior colleagues by accessing recordings of their analysis sessions.
- Scalability: ANY.RUN’s cloud service model allows for easy scaling of security operations by simply adding more licenses.
For a closer look at how ANY.RUN can benefit your security team, contact ANY.RUN for a personalized guided tour of the platform.