Nearly 10 million devices fell victim to data-stealing malware in 2023, Kaspersky Digital Footprint Intelligence has revealed, drawing from insights gathered from infostealer malware log files traded on underground markets. With cybercriminals pilfering an average of 50.9 login credentials per infected device, the threat posed by data-stealers is growing for both consumers and businesses. The .com domain leads in compromised accounts, followed by domain zones associated with Brazil (.br), India (.in), Colombia (.co), and Vietnam (.vn).
In light of this growing threat, Kaspersky has launched a dedicated landing page to raise awareness of the issue and provide strategies for mitigating associated risks.
About 10,000,000 personal and corporate devices were compromised with data-stealing malware in 2023, amounting to a 643 percent increase over the past three years, Kaspersky Digital Footprint Intelligence data shows.The data on infected devices stems from the dynamics of infostealer malware log-files actively traded in the underground markets and monitored by Kaspersky to help companies ensure the security of their clients and employees.
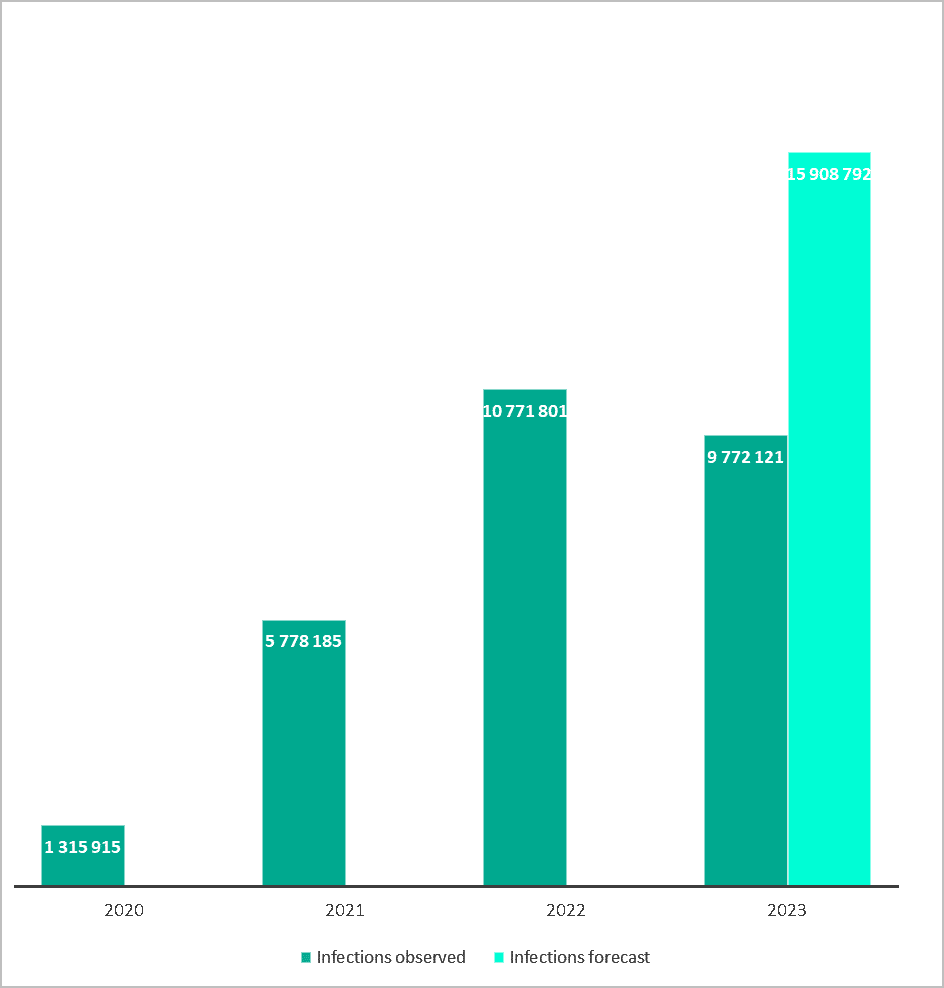
The number of infections with data-stealing malware, 2020-2023. Source: Kaspersky Digital Footprint Intelligence
Even though the number of log-files – and therefore infections – in 2023 has only experienced a marginal decline of 9 percent compared to 2022, it doesn’t imply that cybercriminal demand for logins and passwords has stagnated. It is possible that some credentials compromised in 2023 could be leaked to the dark web at some point during the current year. Therefore, the actual number of infections is likely to be even higher than 10 million. According to Kaspersky’s assessment of infostealer log-file dynamics, the number of infections that occurred in 2023 is projected to reach roughly 16,000,000.
Cybercriminals steal an average of 50.9 login credentials per infected device. Threat actors either utilize these credentials for their own malicious purposes, including perpetrating cyberattacks, or sell or distribute them freely on dark web forums and shadow Telegram channels.
These credentials may encompass logins for social media, online banking services, crypto wallets, and various corporate online services, such as email and internal systems. According to Kaspersky’s data, 443,000 websites worldwide have experienced compromised credentials in the past 5 years.
Regarding the number of compromised accounts, the .com domain takes the lead. Nearly 326 million logins and passwords for websites on this domain were compromised by infostealers in 2023. Next is the .br domain for Brazil, with 29 million compromised accounts, followed by .in, associated with India, with 8 million, .co (Colombia) with nearly 6 million, and .vn (Vietnam) with over 5,5 million.
| Top-level domain extension | Number of compromised credentials per domain, 2023 | |
| 1 | .com | 325,900,000 |
| 2 | .br | 28,800,000 |
| 3 | .in | 8,200,000 |
| 4 | .co | 6,000,000 |
| 5 | .vn | 5,500,000 |
“The dark-web value of log files with login credentials varies depending on the data’s appeal and the way it’s sold there. Credentials may be sold through a subscription service with regular uploads, a so called “aggregator” for specific requests, or via a “shop” selling recently acquired login credentials exclusively to selected buyers. Prices typically begin at $10 per log file in these shops. This highlights how crucial it is both for individuals and companies – especially those handling large online user communities – to stay alert. Leaked credentials carry a major threat, enabling cybercriminals to execute various attacks such as unauthorized access for theft, social engineering, or impersonation”, says Sergey Shcherbel, expert at Kaspersky Digital Footprint Intelligence.





















