Poorly secured remote access attracts ransomware gangs but used to implant coin miners and backdoors too
ESET researchers, based on telemetry, confirm a significant uptick in the number of unique clients who have reported brute-force attack attempts blocked via ESET’s Network Attack Protection and its new layer, ESET Brute-Force Attack Protection.
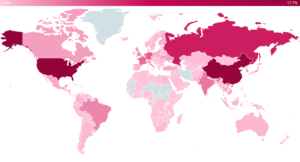
The trend has been observed since the onset of the global pandemic. The COVID-19 crisis has radically changed the nature of everyday work, forcing employees to manage large parts of their jobs via remote access. Cybercriminals – especially ransomware operators – are aware of the shift and attempt to exploit the new opportunities and increase their illicit earnings. In the period between January 2020 and May 2020, the United States, China, Russia, Germany and France topped the list of countries with most IPs used for brute-force attacks.
“Before the lockdown, most employees worked from the office and used infrastructure monitored and controlled by their IT department. But the coronavirus pandemic has brought a major shift to the status quo. Today, a huge proportion of ‘office’ work occurs via home devices, with workers accessing sensitive company systems through Windows’ Remote Desktop Protocol (RDP), a proprietary solution created by Microsoft to allow connecting to the corporate network from remote computers,” explains Ondrej Kubovič, ESET Security Research & Awareness Specialist.
“Despite the increasing importance of RDP, as well as other remote access services, organizations often neglect its settings and protection. Employees use easy-to-guess passwords, and without additional layers of authentication or protection, there is little that can stop cybercriminals from compromising an organization’s systems,” Kubovič continues.

According to ESET telemetry, most of the blocked IPs in January–May 2020 were seen in the United States, China, Russia, Germany and France. Countries that had the largest proportion of targeted IPs were Russia, Germany, Japan, Brazil and Hungary.
RDP has become a popular attack vector in the past few years, especially among ransomware gangs. These cybercriminals often brute-force their way into a poorly secured network, elevate their rights to admin level, disable or uninstall security solutions, and then run ransomware to encrypt crucial company data.
However, other malicious actors try to exploit poorly secured RDP to install coin-mining malware or create backdoors, which can be used in case their unauthorized RDP access has been identified and closed.























